You can’t prevent a zero-day attack, but you can be ready to respond to one. When it comes to zero-day threats, the best defense is definitely a good offense!
Zero-day attacks exploit a vulnerability discovered in software that developers haven’t had a chance to fix (a deeper explanation here). Part of what makes these attacks so devastating is most companies don’t know they’re vulnerable until they’re attacked.
And the most serious vulnerabilities can be exploited over the internet simply by doing business online, opening an email, or having a mobile app.
How prevalent are zero-day attacks?
Zero-day attacks are common — bad actors like to exploit zero-day vulnerabilities. And while the security community jumps into action to stop them quickly, it’s not fast enough for many companies. A recent Ponemon Institute survey found:
- 60% of breach victims were breached due to an unpatched known vulnerability where the patch was not applied
- 62% were unaware that their organizations were vulnerable prior to the data breach
- 52% of respondents say their organizations are at a disadvantage in responding to vulnerabilities because they use manual patching processes
In 2022, malicious actors weaponized 55 zero-day vulnerabilities, according to threat-intelligence expert Mandiant in the report Move, Patch, Get Out the Way: 2022 Zero-Day Exploitation Continues at an Elevated Pace. Millions of companies run software with weaponized vulnerabilities.
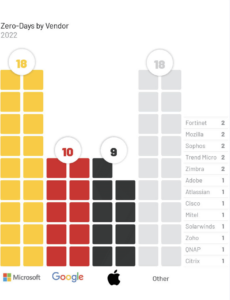
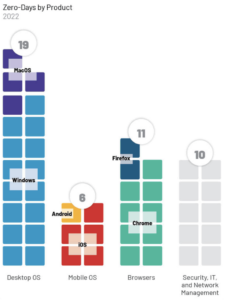
Mandiant’s report shares plenty of valuable data and information, including:
- The big three software companies have the most zero-day vulnerabilities
- Zero-day vulnerabilities continue to grow
- The types of software targeted in zero-day attacks continue to evolve
- Vulnerabilities in Internet of Things (IoT) devices and cloud solutions are now attack targets
Who’s attacking and why?
In 2022, most zero-day attacks originated from China, North Korea, and Russia. The most common motivation? Espionage.
The attack groups are also well-funded. It’s resource-intensive to discover and weaponize tiny software flaws, such as missing data encryption or authorizations, broken algorithms, or password security problems. But to the countries that want to attack U.S. firms and hurt our economy or government, it’s worth the price.
The Chinese state-sponsored threat group APT41, for example, has been exploiting zero-day vulnerabilities for years. Recently, it stole at least $20 million in U.S. Covid relief benefits and countless data through vulnerable internet-facing web applications. APT41’s zero-day attack on Apache’s Log4j, an app used by millions of computers worldwide to run internet services, was especially big news because of its scope.
APT41 is just one hacking group. Researchers don’t know the total number of hacking groups worldwide.
How do “bug bounties” prevent zero-day attacks?
Big software companies pay hackers to find and successfully exploit unknown vulnerabilities in their software and then tell the companies how they did it — the payment is called a bug bounty.
Everyone wins. Software companies find and patch vulnerabilities, hackers make money by doing good instead of bad, and developers can push out the patches before malicious actors discover the vulnerabilities. Bug bounties also foster collaboration in the security community, which helps improve cybersecurity for everyone.
Why would a hacking group attack your mid-market company?
Your company may be a target because of your industry (financial services and manufacturing companies are often targets), your high-profile executives, the fact that you do business with a government agency, or a dozen other reasons.
But most state-sponsored attacks aim to steal user data, not money or state secrets. So you’re just as likely to get caught up in a non-targeted attack as any other company using vulnerable software.
How should you prepare for a zero-day attack?
The good news is you can mitigate some risk from zero-day attacks — follow the same guidelines as you would to Qualify For Cyber Insurance.
You should also invest in threat intelligence feeds to alert your team about new known vulnerabilities and a vulnerability management solution to identify whether or not your particular software configuration makes you vulnerable. Also, use pre-built scripts that are ready to go so you can take action when a zero-day vulnerability becomes known.
The key here is “known.” You don’t want to be caught off guard like the 62% of zero-day attack victims who didn’t know about the vulnerability before they were attacked.
The Mandiant report points out, however, that cloud vendors don’t always make their vulnerabilities public. While they can deploy patches on behalf of customers, greatly reducing exposure time, they also tend to leave customers in the dark during the time it takes to create the patch.
Being in the dark does not help you prepare or react. Mandiant recommends security teams shine a light by being proactive:
- Prioritize patching efficiently and effectively
- Analyze the types of actors that typically target your geography or industry
- Study the tactics, techniques, and procedures that malicious actors use
- Know which products you use provide the largest attack surfaces
- Configure Microsoft, Google, and Apple products properly while allocating resources to defend other software as well
- Follow best practices for network segmentation and least privilege (ZTNA)
People and process
You’ll notice Mandiant’s recommendations don’t focus on technology solutions — instead, they focus on the expertise and diligence of the people tasked with managing risk for your organization.
Even if you can afford the best security technology in the world, it’s the people and processes that run your technology that save the day.
MSSPs that operate a sophisticated Security Operations Center (SOC), such as Leapfrog, routinely manage zero-day vulnerabilities and deal with zero-day attacks. Leapfrog’s CyberRisk Program takes risk management even further by covering attack vectors beyond IT — the people, processes, and facilities that interact with your IT so it works as it should. Reach out to Leapfrog to learn how decades of managed IT and cybersecurity experience protects you against risk from zero-day attacks.

