CyberRisk Program.
Securing your entire organization from cyber risk takes more than secure IT operations — your people, processes, and facilities need to be part of your risk management strategy. Leapfrog’s CyberRisk Program covers all the bases to build a Ring of Security around your organization.
Manage risk with the Leapfrog CyberRisk Program
Leapfrog’s approach to cyber risk management is strategic and comprehensive — it starts with understanding your business risks and what you need to protect and builds a program of integrated solutions that meet your security requirements. Your program:
- Addresses all attack vectors
- Applies our proven security framework
- Identifies gaps and executes solutions
- Manages and maintains security operations
- Continually integrates emerging cybersecurity requirements

Defend your organization using a proactive, comprehensive approach.
With the Leapfrog CyberRisk Program’s centralized risk management approach, there are no weak links. You have a complete program that covers all the bases and management that operates holistically:
- Adheres to best-practice cyber risk strategies
- Scores and tracks relevant security maturity areas
- Builds and updates your security roadmap
- Costs out and prioritizes security initiatives
- Implements your security program
- Establishes and manages governance and risk compliance
- Fills security staffing gaps, including vCSO services

Build a Ring of Security that goes beyond IT
IT infrastructure is less than half of your attack surface — companies must address 100% of attack surfaces to be secure. The Leapfrog CyberRisk Program approach to cyber risk strategy and management addresses all four areas that criminals exploit.
People
While the human operating system is a company’s most valuable asset, it’s also the most vulnerable. Security awareness training and technology strategies protect your IT environment from human error and malicious intent.
Process
Manage risk by managing processes and compliance controls across the entire organization. Due diligence matters — focus on processes to guard against external threats, including third-party risk, and improve protection and efficiency.
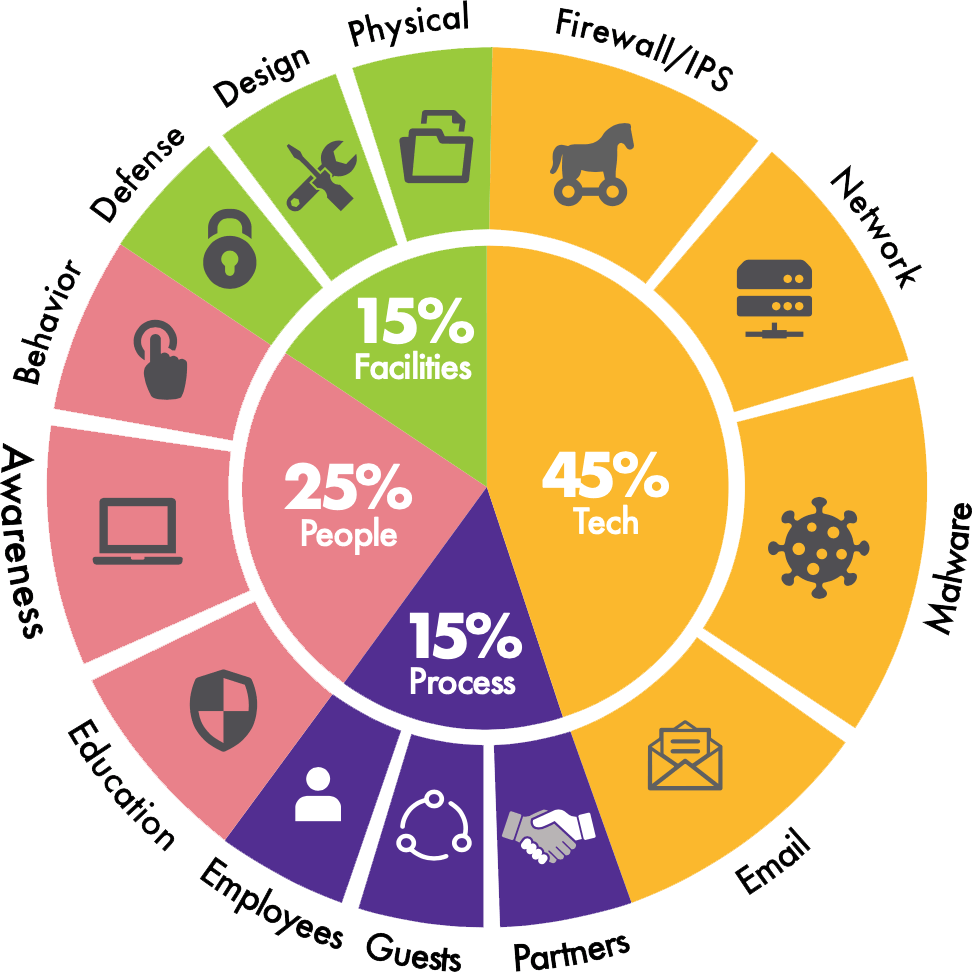
Technology
The right technology solutions are at the core of your cyber risk strategy. Today’s threat landscape is so vast that most businesses find it impossible to keep up. Nonstop technology monitoring and management by an MSSP is your best option.
Facilities
Protect your organization and assets while instilling confidence in your team that they’re safe at work. It’s not enough to protect your digital asset perimeter — you need comprehensive visibility into your facilities to protect things that matter.
Customize your Leapfrog CyberRisk Program.
Your program will include the services you need based on your unique organization and goals.
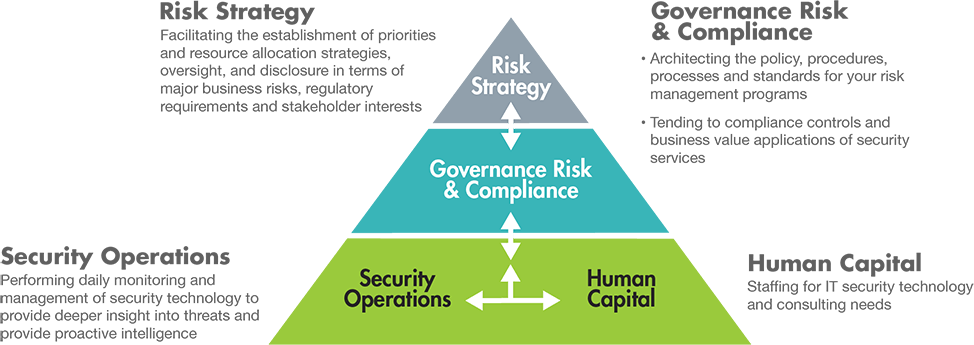
Implement security changes without slowing down your business
When managing your CyberRisk Program, we work in a specific order of operations, each with a distinct phase. Each phase is proactive, overseen, and implemented in close coordination with the security leadership within your organization:
- Understand your business risk to develop your security strategy
- Design and deploy security solutions
- Continually manage all of the elements in your CyberRisk Program
- Enhance your program as threats and business goals evolve
Add a Virtual Chief Security Officer (vCSO).
If you don’t have executive level security management on staff to run your CyberRisk Program, a Leapfrog vCSO provides risk management leadership at a fraction of the cost of a full-time CSO:
- Executive with proficiency in all areas of security and information risk management
- Expert that provides industry best practices, direction, and strategy for all security decisions
- Owner of your security and risk management strategy, which is aligned with your objectives
- Professional who offers services that scale with your business
Ready to learn more about the Leapfrog CyberRisk Program?
Our security consultants are ready to explain the program as it relates to your specific security concerns and answer any questions you may have about how our CyberRisk Program can help you avoid cyber loss.
