Security management.
99% Client confidence in Leapfrog security over the past 10 years.
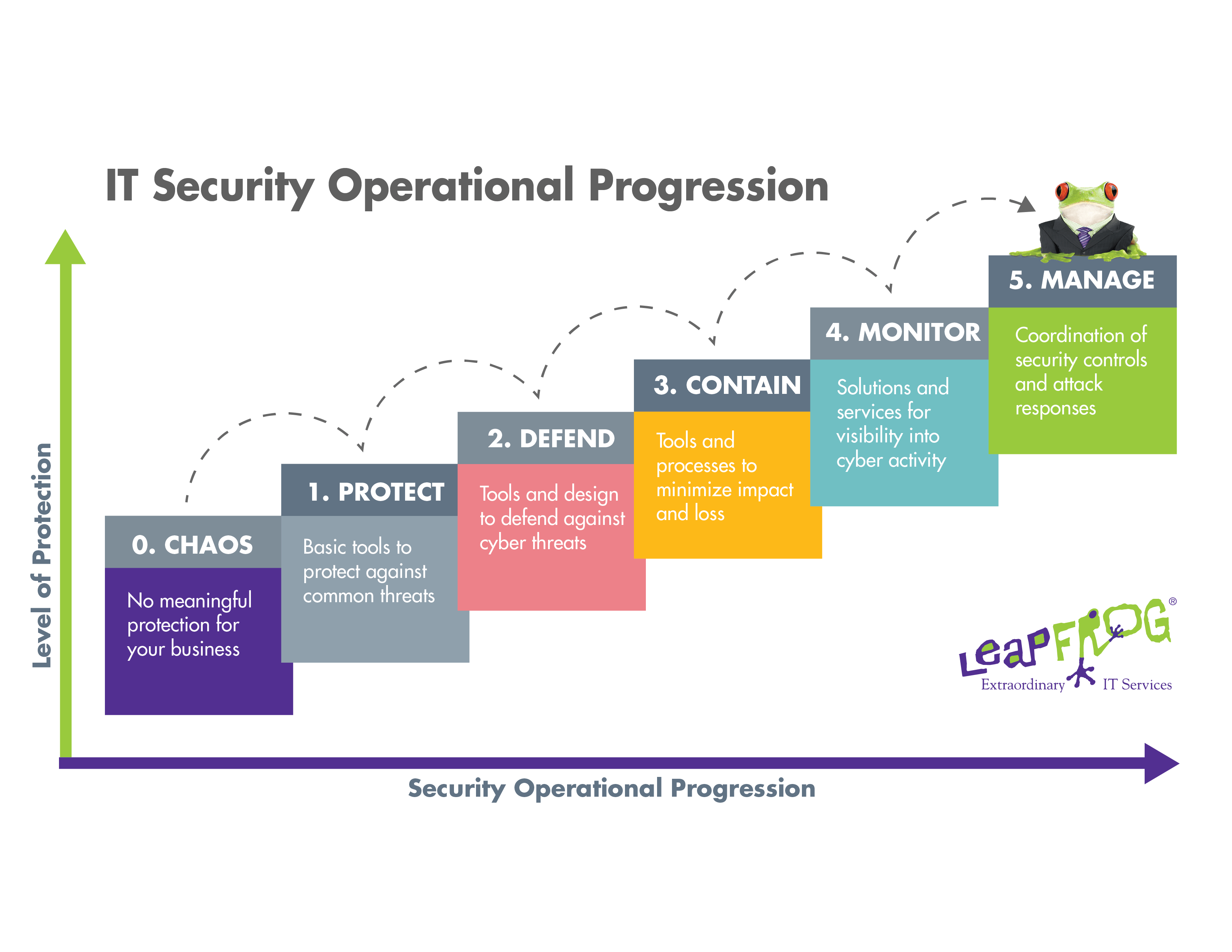
Match the level of threat protection to your business needs.
The right amount of protection for your unique organization involves investing in building and maintaining levels of security that align with your business needs.
One way to think about the level of security you need is to understand that it’s a progressive process. You need to attain competency in one area so you can build the next. Leapfrog uses the IT Security Operational Progression below to illustrate how your organization methodically builds increased levels of protection. The lower end of the scale focuses on protecting and defending your organization and the higher end includes proactive activities that can be tailored to your business to contain, monitor, and manage cybersecurity. Businesses at the highest levels use advanced tools and processes with visibility that allows for faster responses to new threats and attacks. Automation provides the fastest response.
Leapfrog can add threat intelligence — such as automated threat detection, automated threat response, and identity-based access control — to your system if it makes sense for your business.
To ensure you don’t outspend your risk, we can adjust your security strategy as your needs evolve.

Protect every part of your environment.
Leapfrog uses established security standards to manage each area of your IT:
Cybersecurity
Continually protect your network, computers, apps, and data against external threats, attacks, ransomware, and unauthorized access.
Data and Network Security
Guard against internal threats (human error and intentional) through concise network controls and permissions.
Compliance
Disaster Recovery (DR)
Understand why securing your IT is so complex.
It’s challenging to build a security program from scratch and operate it effectively — the number of details that fall under each security discipline can be enormous. Leapfrog clients appreciate that our security professionals have designed a robust security program. It operates smoothly, doesn’t slow down their businesses, and can be customized for their specific needs.
By relying on Leapfrog’s proven security program, your environment is better protected without having to build, operate, and maintain your own program. Our security professionals focus on operating these six disciplines:
- COBIT
- ISO/IEC
- NIST
- PCI
- SAN S/C SC
- SOC 2
- Security engineering
- Network design
- Data protection
- Cryptography and encryption
- Access control
- Cloud security
- Cloud access security broker (CASB)
- Identity management
- Federated identity
- Physical security
- Baseline configurations
- Secure system builds
- Security operations center (SOC)
- Business continuity management
- Prevention
- Active defense
- Detection
- Recovery
- Vulnerability management
- Security incident and event management (SIEM)
- Data leak protection (DLP)
- Incident response
- Investigation
- Breach notification
- Forensics
- Containment
- Eradication
- Disaster recovery (DR)
- User education
- Business-risk tolerance review
- Assets inventory and valuation
- Vulnerability scanning
- Data-centric risk assessment
- Penetration testing
- Blue team/Red team simulations
- Third-party risk protection
- Fourth-party risk protection
- Code review
- Audit
- Company Written Supervisory Procedures (WSPs)
- Reports and scorecards
- KPIs and KRIs
- Indicators of compromise (IOCs)
- Threat contexts: people, systems, syndicates
- White hat/Black hat threat actors
- Community-based intelligence sharing