Cybersecurity.
Respond to growing threats.
We’ve become more connected since the pandemic — internet traffic is estimated to be about 50% higher now. More digitalization has led to more opportunities but also more cyberattacks that are more expensive and damaging.
Today, the average data breach costs $4.62 million with lost business opportunities representing 65% of the cost. Ransomware accounts for 25% of all breaches (up 13% since last year), phishing for 16%, and cloud misconfiguration for 15% (IBM).
New threats are piling on top of the usual suspects — you need to guard against cyber risk from older systems, zero-day threats, poorly protected endpoints, and geopolitically motivated disruptions in addition to everything else.
What’s the best way to safeguard your IT environment and recover quickly when you have an incident? Team up with an IT partner that uses a consistent methodology with security that’s built-in.
Related: Report Highlights Vulnerabilities That Put 30,000 Machines at Risk

Learn 11 ways to protect your company from ransomware: Is Your Organization Ransomware-Ready?
The Leapfrog CyberRisk Program
The right methodology keeps you safe and offers peace of mind — 99% of Leapfrog clients report having confidence in Leapfrog security over the past ten years.
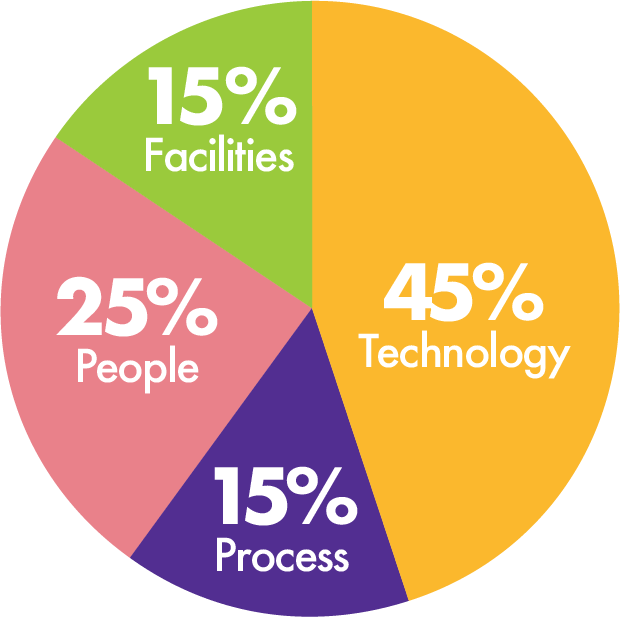
Still, many companies need to improve their cybersecurity beyond IT to stay secure in today’s threat environment. Technology represents only 45% of potential attack vectors, and the other 55% includes your people, processes, and facilities. Your best defense against cyber loss is a proactive risk management strategy that covers all cyberattack vectors by creating a ring of security around your entire organization.
The Leapfrog CyberRisk Program approach offers a customizable, holistic approach to cybersecurity risk management that can include:
- Risk Strategy — Develop security plans and oversee program management
- Governance Risk & Compliance — Architect and manage policy, procedures, processes, and standards
- Security Operations & Human Capital — Monitor and manage constantly and provide IT security staff and consultants as needed
Strengthen your weakest link.
Even the best cybersecurity tools and processes can’t protect your company from employees who inadvertently open the door for hackers. Cybercriminals target employees who are most likely to fall prey to social engineering and use other effective schemes, including spray-and-pray.
Stolen credentials, phishing, misuse, or human error account for 82% of all breaches — that statistic from the Verizon 2022 Data Breach Investigations Report is likely to get every organization’s attention.
Your best defense against the lion’s share of cyberattacks is regularly training and testing your entire team, including your C-suite. This is why Leapfrog partners with a global leader for security awareness training and other training experts.
RELATED: Cybercriminals Are Using ChatGPT for Phishing — What Should Your Company Do?

Protect all of your endpoints all of the time. Download Making Sense of EDR and the Cyber-Insurance Connection.
Protect and defend with good cyber hygiene.
Healthy IT environments are less likely to be breached. To beat hackers at their game, make sure to keep up with cybersecurity basics consistently — good cyber hygiene helps protect and defend your company. Leapfrog works with you to:
- Store critical business information on ransomware-resistant backups
- Prevent unauthorized users from accessing your systems
- Implement the latest security controls and apply the latest patches and updates immediately
- Encrypt your data and devices
- Secure email
- Replace or retire hardware and software that’s reached end of life
- Monitor your endpoints for threats with an Endpoint Detection and Response (EDR) solution
- Complete any other hygiene activities required for your environment
Contain and monitor to up your game.
To further reduce your risk, take cybersecurity to the next level. Leapfrog follows the ITIL process and adheres to the security standards of your choice (NIST, ISO, others). Our iterative risk evaluation process informs which security enhancements we recommend to contain and monitor threats. They may include:
- Minimizing exposure with network segmentation and firewall policy-based boundaries
- Enabling the latest security controls for your network, cloud platforms, and endpoints
- Monitoring for stolen or compromised credentials
- Performing vulnerability management
- Classifying and protecting all data based on sensitivity level
- Implementing protections that limit third-party risk
- Leveraging third-party expertise, such as considering penetration tests
Part of our methodology is to put all processes and policies in writing and practice for emergencies. If you need to comply with regulatory requirements, we have you covered there, too — Leapfrog is SSAE-18 SOC 2, PCI, and CMMC compliant.