Methodology.
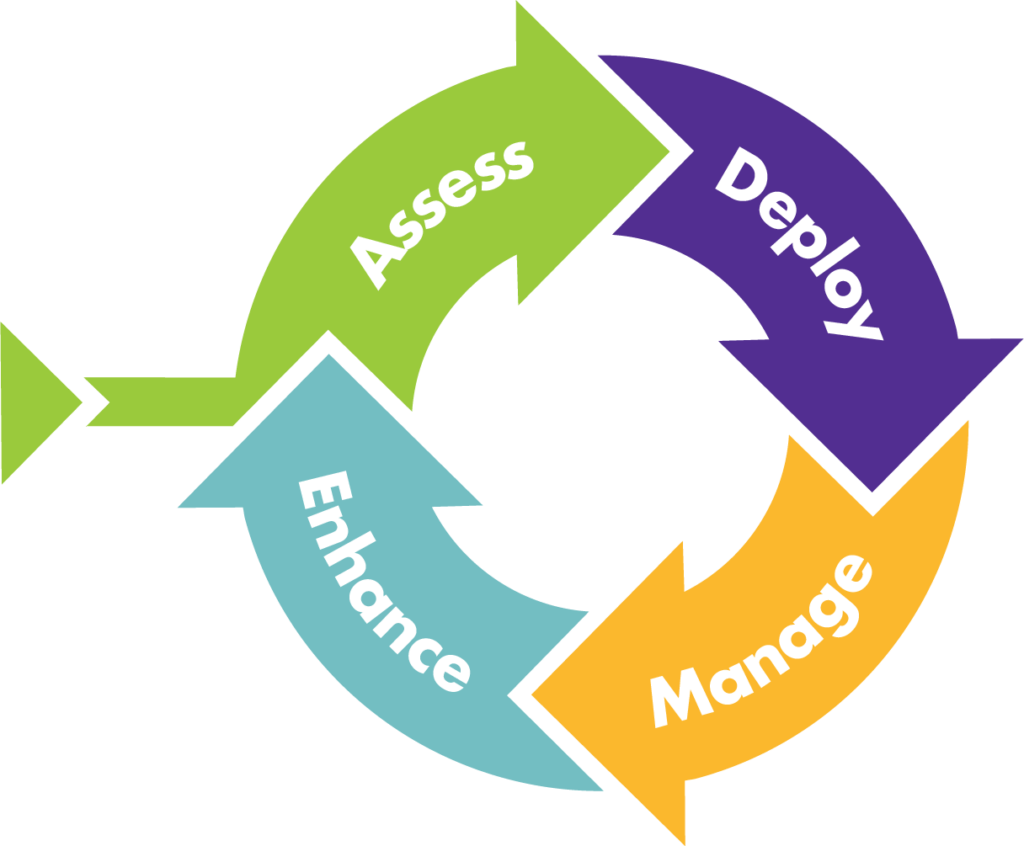
The Leapfrog Methodology is a cycle — assess, deploy, manage, and enhance. Each year we assess your needs again so we can keep your business leaping ahead.
Use the Leapfrog Methodology to link your IT strategy to your business strategy.
When your IT strategy aligns with your business strategy, it’s the recipe for getting things done.
Even if your IT systems are all working properly, your IT strategy can still be out of alignment if it doesn’t include the tools, processes, and expertise you need to get the business results you want. The right IT strategy is based on your business goals and determines the right technologies. With Leapfrog’s proven methodology, your IT environment is secure, reliable, scalable, high-performing, holistic, and, of course, aligned.
And ready for new opportunities.
Continually manage and improve your IT — the Leapfrog Methodology builds on itself.
The Leapfrog Methodology starts with understanding your business and identifying IT challenges. After designing and deploying updated solutions in a way that minimizes disruptions to your company, we move into the management phase. While managing your IT, we continually secure and optimize your IT environment to align with your business goals.
- Assess. Analyze and evaluate to build your IT roadmap
- Deploy. Transition and modernize based on strategic design
- Manage. Proactively maintain and operate IT while providing end-user support
- Enhance. Constantly optimize your environment to keep you secure and productive
Our CyberRisk Program follows a similar cyclic and programmatic approach to secure your entire organization from cyber loss.
Along with the right methodology comes the right team, tools, and processes.
Even IT professionals who spend their days making IT decisions can get stuck deciding between technology options — which will best meet their needs now while remaining flexible for future needs? Which will integrate seamlessly with their existing systems? How can they transition to updated solutions without slowing down business? What’s the most important thing to do first?
The Leapfrog Methodology removes the guesswork.
We developed our methodology to answer questions like these and provide our partners with technology guidance, implementation, and ongoing support. The IT roadmap we develop for you is based on your goals and our findings during the assessment phase. It solves any immediate problems, defines needed improvements in priority order, and lays out a reasonable cadence to move forward. Leapfrog manages what we design and build and co-manages IT environments with in-house IT teams.

Keep increasing IT performance and you'll keep getting more business value from your IT.
The process of continually benchmarking, road mapping, and improving your IT is the guiding principle behind the Leapfrog Methodology. It enables your company to systematically move up the IT Maturity Scale, which is a measure of how well your company is adhering to IT industry best practices.
The higher up you are on the IT Maturity Scale, the more your IT can empower your business.
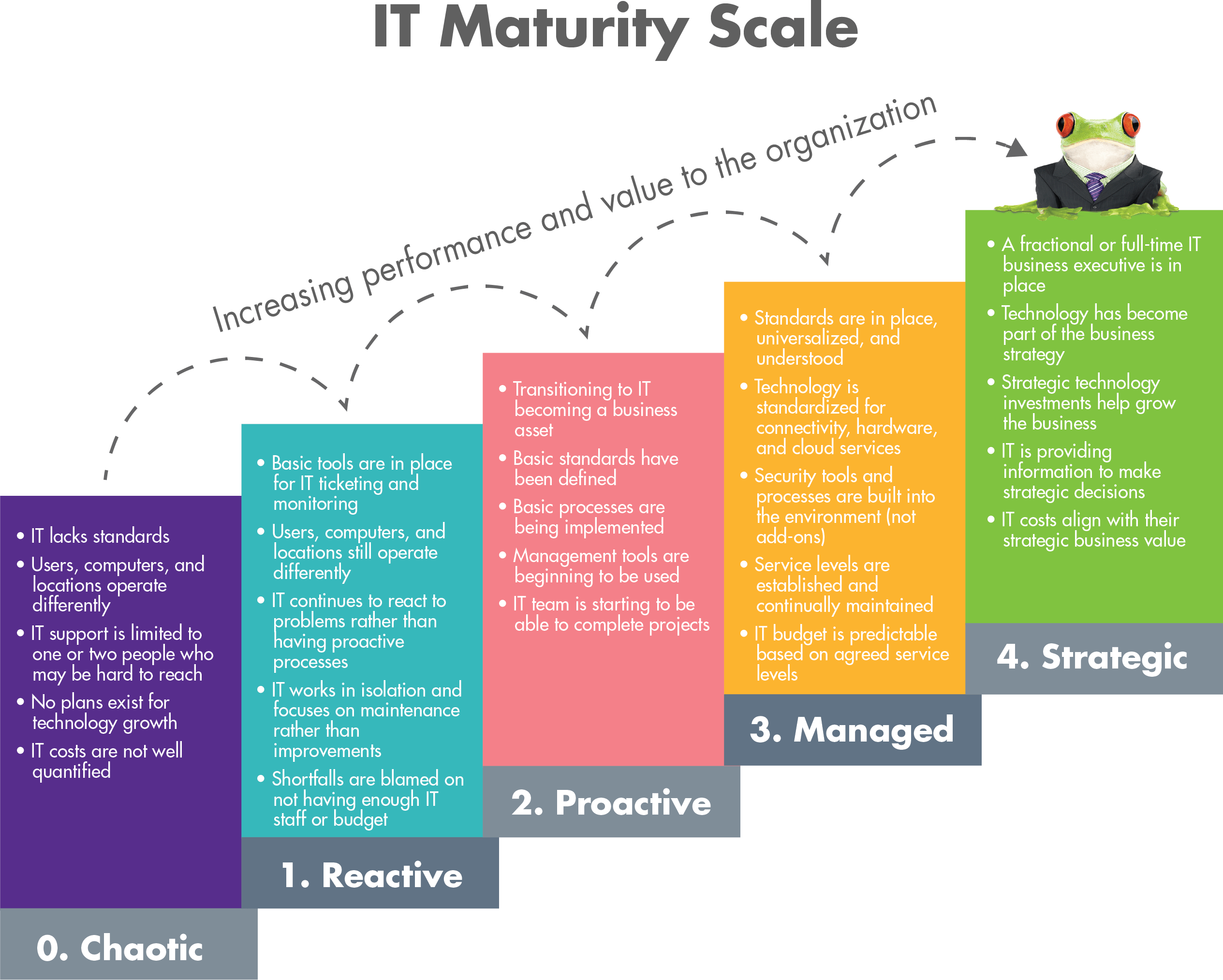
The IT Maturity Scale represents the progression from chaotic to strategic. You may notice that the bottom two levels are related to operational activities, and the top two are related to service levels. The middle level, the Proactive level or Level 2, is the transition where your IT is becoming an asset to the business. In determining where your company currently falls on the scale, you may find you have some characteristics in a few different levels — this is typical.
To get the most business value from your IT, it’s best to master each level as you progress up the scale so you can build on your proficiencies.
Leapfrog’s targeted minimal operating level for IT efficiency is the Managed level or Level 3. Our methodology is designed to get every client to Level 3 as fast as your budget and change tolerance will allow.
Transition and improve smoothly — the Leapfrog Methodology makes it easy.
Part of the Leapfrog Methodology is ensuring that the transition to working with Leapfrog is easy for everyone at your organization. As a service company, we prioritize your ability to keep doing business effectively at all times, including during the transition period.
The transition to Leapfrog is designed, planned, and scheduled with your internal team to have minimal impact on your operations and require as little effort on your part as possible.
The goal is for your teams, customers, and stakeholders to be unaware that changes are taking place — to fix the plane while it’s flying. Onboarding sessions with your employees, if needed, are included. Judging by the responses we get from our clients immediately after the transition and continuing throughout our partnerships, the Leapfrog Methodology more than meets expectations.

Take the first step toward simplifying and securing your IT by adopting the Leapfrog Methodology.
We invite you to contact us today if you’re ready to find out how the Leapfrog Methodology can help you resolve technology issues and improve business results. It’s time to leap ahead with a systematic approach to simplify and leverage your IT.