The rapid shift to digital technology has made companies more vulnerable to cyber attacks — to protect against cyber loss, you need to secure all your attack surfaces. Leapfrog secures your IT and goes beyond technology to address the other vulnerabilities that put your network at risk.
Leapfrog is proud to have sponsored the 2023 CISO Atlanta Summit — thank you for attending this informative event.
Securing IT and the processes that use it.
Cyber risk management for mid-market companies.
…An employee clicks a ransomware link by mistake.
…A vendor fails to properly complete a software patch, leaving one of your systems vulnerable.
…A thief dressed as a utility worker sneaks into your facility alongside employees returning from lunch.
Even if your technology is perfectly secure, your company is still vulnerable to cyber risk from other attack vectors. Your IT represents less than half of your cyberattack surface. The other half is made up of non-technical risks — poorly trained or hurrying employees, undefined or unverified processes, facilities that aren’t properly defended, and dozens of other gaps that can put your company at risk.
Mid-market companies concerned about cyber loss need to address cyber risk
holistically. A single partner that can protect the entire attack surface, both technical and non-technical is the most effective approach.

Cybersecurity that goes beyond IT.
Leapfrog Services completes the Ring of Security around your technology, people, processes, and facilities by combining secure IT operations with a comprehensive risk strategy and governance activities. Our strategic approach to cyber risk management includes:
- High-performing, secure IT that works seamlessly
- Governance expertise of a CSO
- Technology expertise of an MSP/MSSP
- Top-tier technology partners
- Optional V-CSO and advisory services
Following a plan that identifies and closes security gaps in priority order is the best way to reduce the likelihood of cyber loss.
Leapfrog’s proven methodologies are based on industry best practices and 25+ years of experience in secure IT operations, cybersecurity consulting, and cyber event remediation.
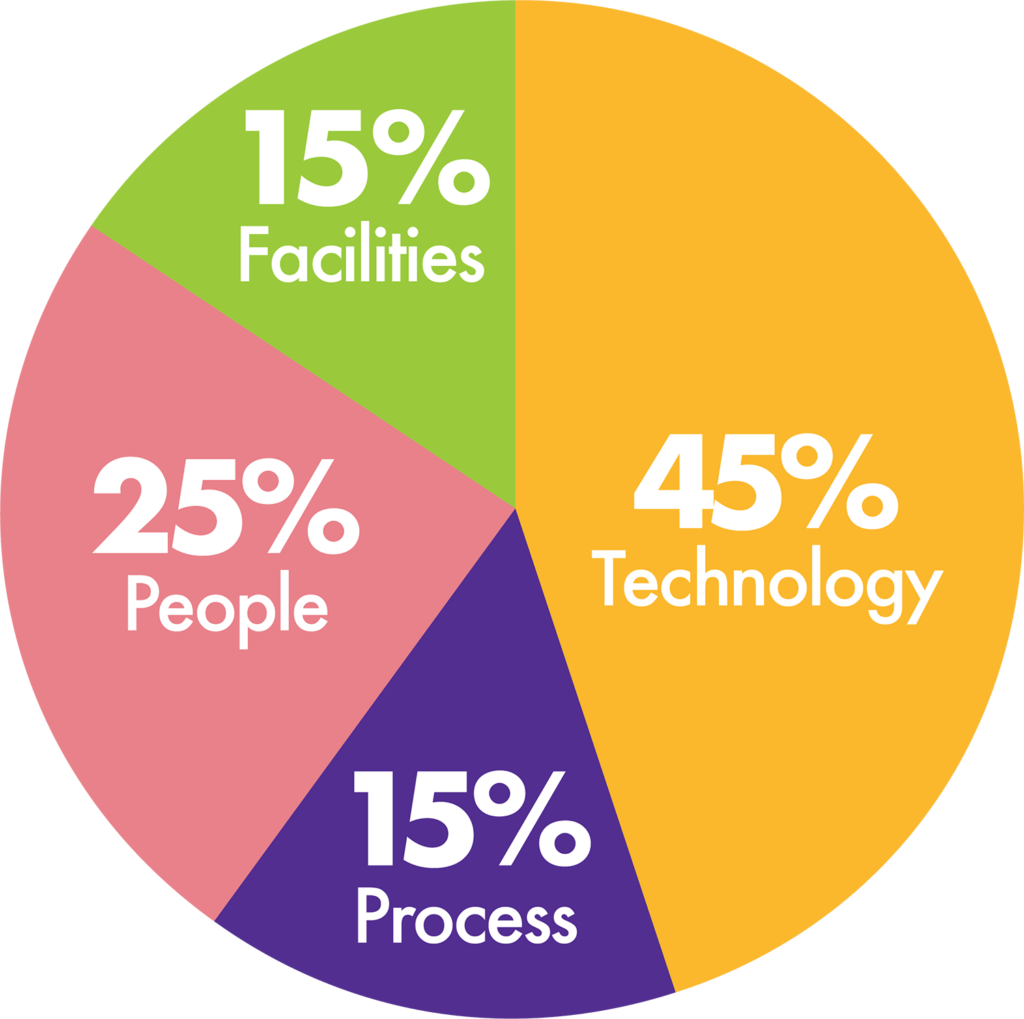
Your cyber attack surface:
45% Technology
55% People, Processes, and Facilities
Learn more about how Leapfrog secures your organization against cyber loss.
- What is the Leapfrog CyberRisk Program?
- How does the Leapfrog Methodology improve your IT operations?
- Who is Leapfrog?
Leapfrog Quick Reference Guide:
19 Questions: Is Your Cyber Risk Strategy Meeting Your Business Objectives?


