We posed a series of questions to Leapfrog Services CTO Emmett Hawkins about what companies should do to improve their security posture after the SolarWinds hack.
To recap what happened, late in 2020, a leading cybersecurity company named FireEye discovered it had been hacked and identified SolarWinds network-monitoring software as the source of the hack. The software had been infected with malware in early 2020 that allowed hackers to secretly access files of more than 100 government agencies, major companies, and universities (higher numbers were reported earlier).
Emmett’s insights cover why this hack is an alarm bell for all organizations and what they should do to prevent their companies from becoming victims of similar hacks.
Q: In a nutshell, what does the SolarWinds hack mean for organizations moving forward?
A: It’s a wake-up call. We all need to take action. This includes everyone from the Department of Defense to Fortune 500s to growing companies to mom-n-pop businesses. What’s so unique about the SolarWinds breach is its scope. We’ve never had this expansive of a breach before (that we know of), so people now have a better understanding of how their companies may be vulnerable in ways they hadn’t considered before. Security is getting a lot of attention right now, which will hopefully also lead to action.
Q: What kinds of specific actions should organizations be taking? It seems the actions could be vastly different, based on the individual company.
A: The actions can be different but they boil down to the same two overarching activities — first, taking inventory of all of your applications and vendors and, second, having visibility into your systems so you can monitor them continually.
You need the inventory to know everything that your systems are connected to because everything is a potential portal for bad actors — your apps, your vendors, your vendors’ vendors, your partners, and the list goes on. Your most important client might follow the right security protocols but what if one of its suppliers doesn’t? It’s all connected.
The other thing you need to do is to be able to see what’s going on with all those potential portals. Having visibility into your systems lets you monitor who is in your systems, when they got in, what they’re doing once they’re there — the only way to know if something isn’t right is to be able to see it happening. This requires vigilant monitoring. Humans don’t typically have the capacity on their own to monitor all this data, especially if the bad actors are being stealthy, and they usually are. Even small companies need to look at using automated tools to spot anomalies that humans can miss.
Q: Let’s talk about doing an inventory of applications and vendors. What’s the process and who is responsible for it? And what do you do with the inventory once it’s complete?
A: To do the inventory, an IT department or IT security partner looks at everything and everyone connected to your network. Hopefully, they’ve been doing this all along as part of their standard operating procedures, but it can be easy for things to slip through the cracks if the inventory isn’t updated each time there’s a change. If your organization doesn’t have the inventory or hasn’t updated it in a while, now is definitely the time. Include every last vendor, app, subscription, and also include the ones you barely use.
As you review the list, make sure you’re running the latest version of everything and review the permissions associated with each account to make sure each person with access really needs it. You should be documenting and tracking all this in one central place.
Q: What do you do if you find security problems as you work through the list? Can you give me an example and who handles the solution?
A: If you find you’re using SolarWinds or another app with vulnerabilities, you can either mitigate the risk or eliminate the risk. A third option is you can accept the risk if it’s not serious, like some bad code in your on-hold music.
But you’re not going to find vulnerabilities just by updating versions and controls. Vulnerability management is a security process by which you dive deeper to evaluate your systems and data to see if they have known security vulnerabilities. It’s a similar process to the hackers’ attack chain — they look for vulnerabilities that can be exploited and so should you. It’s important that the good guys know what the bad guys know.
Most internal IT departments don’t manage for vulnerabilities because that’s not their main goal. Their goal is to ensure the availability and operations of your IT. Managed security’s main goal is to limit, eliminate, and control risk, which is completely different. Sometimes these two different sets of goals can create conflict, most often when security wants to remove a useful tool that may impact network administration.
It’s easiest to visualize the progression of improving your security by using a visual aid like Leapfrog’s IT Security Progression Model (SPM). It shows the IT security progression from chaos, which is having no meaningful protection at all, to activities that protect, defend, contain, monitor, and manage threats. The most secure companies operate on the right (higher) side of the scale.
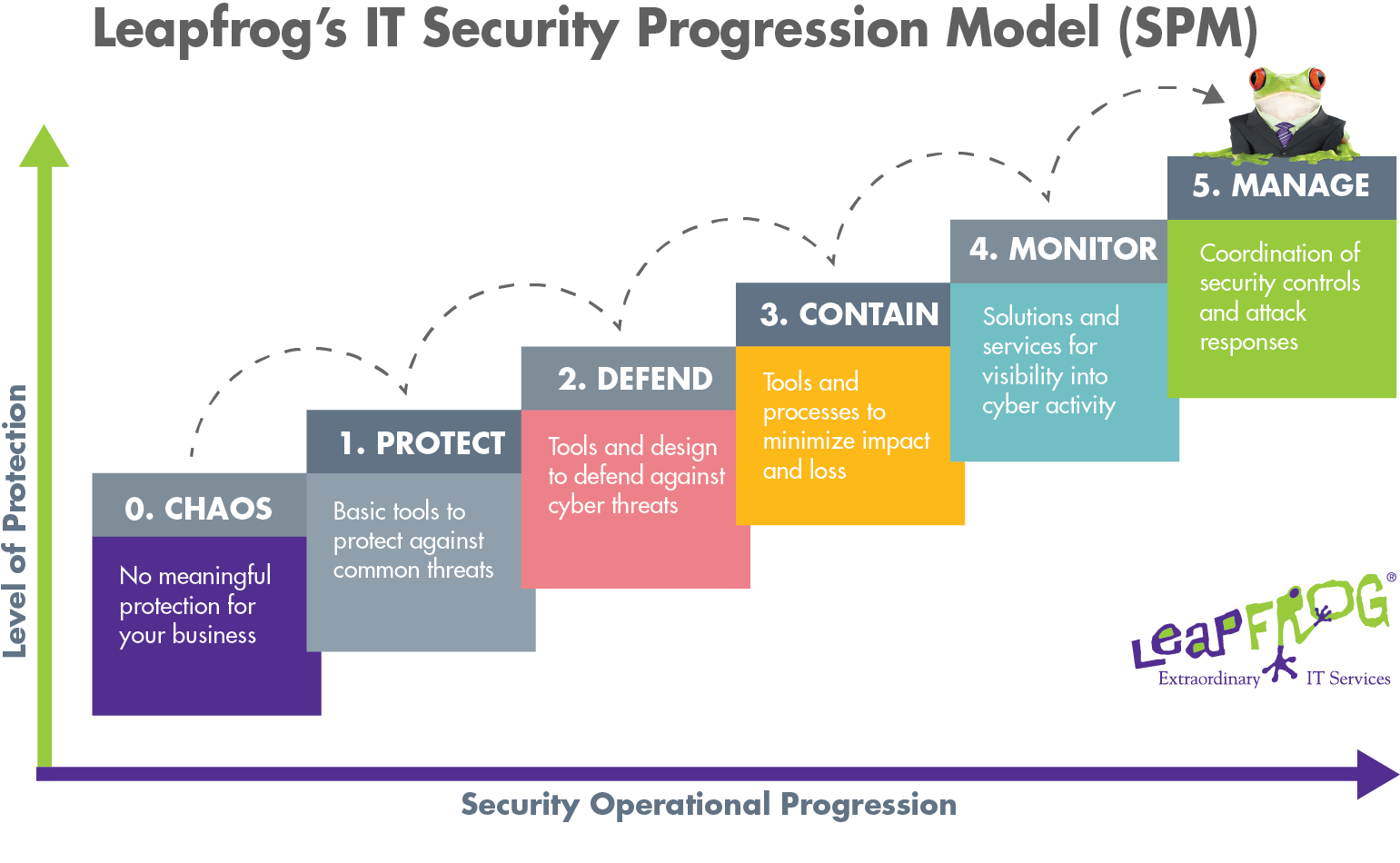
Q: On the model, Monitoring is Level 4 – or close to the top of the progression. Can organizations do some monitoring even if they’re still at Level 2, the Defend level?
A: Yes, they can and they should. It’s OK if your feet are at Level 2 but you’re reaching for Level 4. Companies don’t need to wait to finish mastering one level before they start investing in the next level or two. Monitoring has value, even before you finish Containment to be sure, but you won’t be able to master Monitoring until you’ve fully mastered Containment.
It’s important to keep in mind that the mastery requirements for each level also change over time. What was fine for the Protection level five years ago isn’t fine today. You will find yourself revisiting and reinvesting in previous levels even as you move up the scale. It’s a continual process of reevaluating and refining — threats and technology change constantly.
This is true for Level 5, also. Even though vulnerabilities are the most common way that companies suffer a cyber incident, there’s a difference between crimes of opportunity (vulnerabilities) and targeted attacks. Even when you get to Level 5, you’re not completely in the clear because you can be the victim of a targeted attack, unfortunately.
Q: These security improvements sound critical but not like changes that can be achieved overnight. What kind of timeline can organizations expect as they make these security improvements?
A: It’s up to you how fast you want to move. You can either try to fix what you have, like repairing or renovating your current house, or you could just move into a house that’s already fixed up. Depending on the business, the apps you use, your users, and where you are in the investment cycle, either can be the right choice for you.
If you decide to fix what you have instead of moving your data and employees to a secure environment, the goal is to be continually moving up the security model. Just start with wherever you are now and make improvement after improvement.
The mindset should be that security is an ongoing business practice that keeps your organization as secure as it can reasonably be without outspending your risk. There’s no such thing as set-it-and-forget-it with protecting against vulnerabilities. There are too many bad actors out there trying to make money by stealing other people’s stuff and too many potential vulnerabilities, which the Solar Winds hack proves. Hackers and even nation-states are going to keep getting get better and more creative about what they do. You need to try to stay at least one step ahead of them by keeping your defenses up, your vulnerabilities down, and your company off the hackers’ radar.

